Generate Random MD5 Hashes
Quickly encrypt data with our Random & Unique MD5 Hash Generator. Generate MD5 hashes for enhanced data security. Tool for generate several random md5 hashes. All functionality are completely free.
How to use this Generate Random MD5 Hashes Tool?
How to use Yttags's Generate Random MD5 Hashes?
- Step 1: Select the Tool
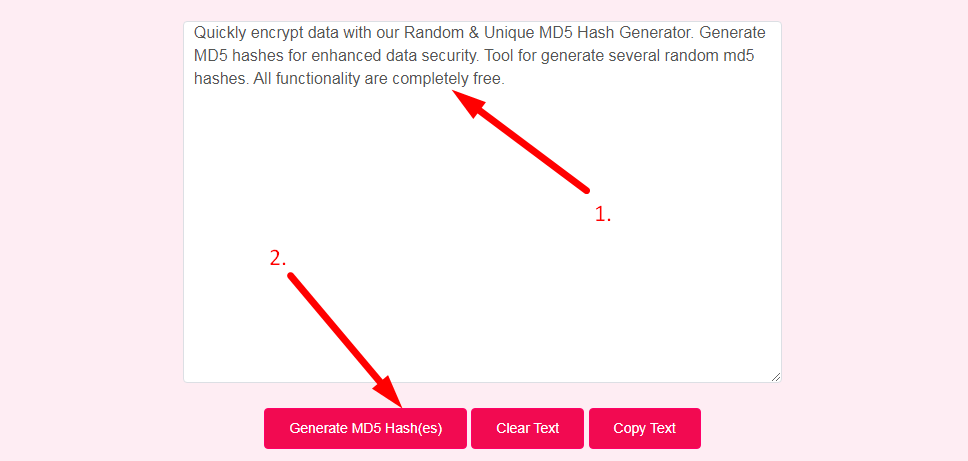
- Step 2: Enter The Text And Click On The Generate MD5 Hash(es) Button
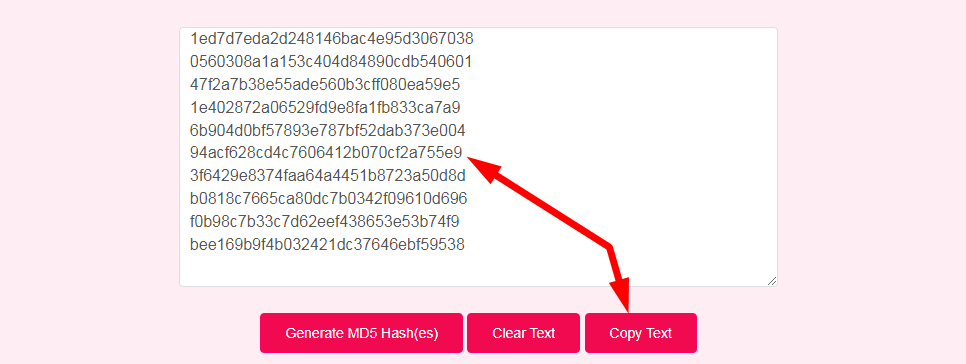
- Step 3: Check Your Generate Random MD5 Hashes Result
A tool for creating an MD5 hash from a string. Use this fast, free tool to create an MD5 hash from a string. Generate random hashes using the MD5 hashing algorithm. MD5 is the most popular hashing function. Hash a string using our free online tool.
If you want to link to Generate Random Md5 Hashes page, please use the codes provided below!
FAQs for Generate Random MD5 Hashes
What is a Generate Random MD5 Hashes?
A "Generate Random MD5 Hashes" tool is designed to create random MD5 (Message Digest Algorithm 5) hash values, often used for testing, cryptographic applications, or as unique identifiers in various contexts.
Why is MD5 hash important?
MD5 is primarily used to authenticate files. It's much easier to use the MD5 hash to check a copy of a file against an original than to check bit by bit to see if the two copies match. MD5 was once used for data security and encryption, but these days its primary use is authentication.
How many combinations are there in MD5 hash?
Note the definition of a hash above which states that a hash is always fixed-length. For example, the MD5 hash is always 128 bits long (commonly represented as 16 hexadecimal bytes). Thus, there are 2^128 possible MD5 hashes.
Is MD5 hash unique for a file?
As with all such hashing algorithms, there is theoretically an unlimited number of files that will have any given MD5 hash. However, it is very unlikely that any two non-identical files in the real world will have the same MD5 hash, unless they have been specifically created to have the same hash.
Is MD5 hash OK to use?
MD5 hashes are no longer considered cryptographically secure methods and should not be used for cryptographic authentication, according to IETF.